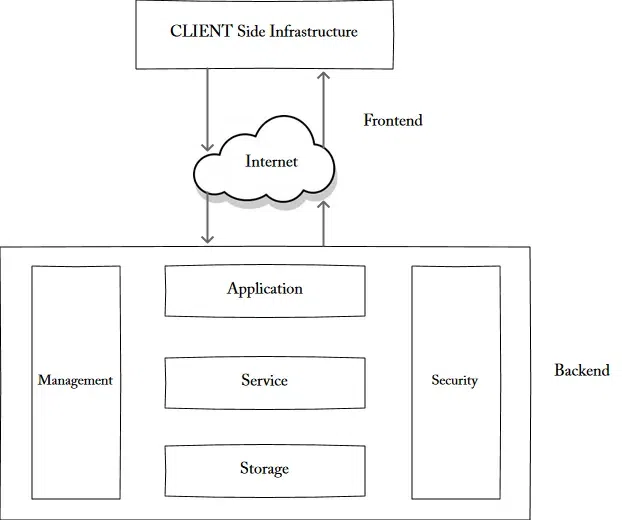
Cloud Computing Security Parameters on Various Cloud Platforms

TL;DR
- Overview of key security parameters in cloud computing, including encryption, access control, and compliance.
- Comparison of security features across major cloud platforms like AWS, Azure, and Google Cloud.
- Emphasis on the importance of monitoring and regularly updating security configurations.
Abstract
Cloud Computing is currently a consistently emerging platform in the IT industry. As of now, big tech giants are providing cloud services to various industries as it is their essential policy to secure the architecture and enterprise data.
With the increase in demand for cloud computing technologies, many tech giants are providing cloud automation services like Amazon Web Service (AWS), Microsoft Azure, Google Cloud Platform (GCP), IBM, SAP, Cloudera, and more.
In the cloud infrastructure, the enterprise’s cyber security aspects come as one of the biggest digital transformation challenges. The serverless computing aspects are more delegated to secure cyber security services and policies, which helps prevent data breaches, cyber-attacks, and other unusual cyber theft activities. This blog includes important cloud security parameters that should be used on various cloud platforms and services.
I. Introduction
Since the 1960s, cloud computing concepts have been introduced by researchers and computer scientists. Due to several loopholes and less computing power in the cloud infrastructure, some huge potential clients and organizations are not adapting to the cloud approach. To overcome this hurdle, in 2006, Amazon launched its cloud platform named AWS (Amazon Web Services), from which the cloud revolution started. This helped to solve loopholes that included analysis of policy and architecture of specific cloud platforms, their comparison, and cyber security aspects.
II. Data Security Aspects in Cloud Computing
Cloud computing undoubtedly delivers exceptionally healthy service to the user, but still, many enterprises do not support cloud computing services because of security constraints. The main security consequences are data security and privacy protection. This security dilemma hinders the managers, customers, or clients from reinforcing the services provided by cloud computing technologies. There should be a faithful and hopeful relationship of trust between customers and managers before availing of any cloud service. The official team must have the certified management team’s commitment to protecting the security risks to secure cloud data. There are lots of risks consolidated with the cloud computing architecture framework. A few of them are:
- Laws and regulation: Laws and regulation boundaries should be defined up to some extent.
- Virtualization risks: Virtualization might not be as good as physical architecture, as its 3rd party architecture and data security trust should build up.
- Strict cyber policies: Lack of standards and auditing, possible uncontrolled costs, etc.
Cloud computing is the virtual environment for the customer which is using the cloud services. It will provide the data to the cloud without being informed about the physical location of the data. The data can be there with lots of other data on the cloud. So the essential provision that storage providers must have are confidentiality, integrity, and availability.
A cloud-based model should be implemented with specific hidden parameters, including firewall restrictions, strong cyber policies, inbound/outbound tracking, encryption and decryption of data, etc. This article provides complete detail of all these parameters in the below-mentioned sections. It also includes pros and cons comparisons based on different cloud provider platforms like AWS, Azure, GCP, IBM, SAP, etc.
III. Key Cloud Data Security Parameters
In today’s cloud-based digital transformation, the client is looking for a platform to adopt cloud framework/services for their data storage management and physical storage security with computation. Also, there are lots more things in cloud security to be taken care of to accelerate the digital journey, like DoS attacks, data breaches, data security, insider infrastructure security threats, etc.
We will discuss various parameters like memory management, concurrency control, load balance, cloud network, database operating systems, virtualization, resource allocations, etc. In a cloud platform, securing all these parameters is essential for CSP and Architect, who set up the whole environment. Also, along with security, service cost is another issue for many cloud service users (customers). So, the cost and security compliance should be considered before deploying the software model on any cloud platform. Sometimes, using unnecessary services sends the project over budget, which is not a positive response.
Several cloud computing platforms like AWS, Azure, IBM, and GCP used encryption, data protection policies, and rules. Let’s discuss a few parameters about the various cloud data security platforms.
A) Encrypt Data Before It Moves to the Cloud
If we don’t want to use cloud encryption policies and services provided by a cloud platform, clients or users are required to pre-encrypt data by themselves before moving data to the cloud. It helps clients and services providers to deal with the cloud operation having a particular ethnicity.
Example 1: Suppose we are moving our database service (back-end) to the cloud database service. In the first step, we will encrypt our data on the local system or local server using specific hashing algorithms. In the second step, we will migrate the data cloud database service. In the third step, finally, we will deploy the past operations live on a cloud instance.
B) Restricting and Securing Access With Cloud Cryptography
Cloud cryptography is another way to protect your computer. Cloud computing service providers like Azure use cryptography to provide a layer of data security at the system level and enable secure access to anyone who needs shared cloud services. This encryption layer depends on the quantum direct key system, a high-level system of compatible encryption keys. It helps users to receive public and private keys with a specific ID. Also, cryptographic cloud computing reduces network congestion.
Example 2: Suppose client engineers want to secure data with specific parameters and encryption services. They can use a symmetric-key system, which has fundamentally essential critical pair system logic — where only one key is used to encrypt and decrypt data information. It is a widely accepted approach to the cloud.
C) Restricting User Access
User restriction is also a crucial constraint to be evaluated during the cloud because unauthorized access can compromise an enterprise’s critical data to the outside world. So enterprises should secure data by building strong data prevention policy.
There will be an identity and access management system in this user access restriction policy, which has a unique authenticator app with a one-time password system. Also, it verifies the user on a real-time authentication basis. It prevents the user from accessing other services available in the cloud platform, which is restricted for the user.
Example 3: Suppose users are back-end developers who have access to the cloud database services, then they can’t get access to instance and server services. Let’s take an instance AWS service; if the back-end engineer has access to S3, RDS, and Lambda service, he can’t access the EC2 service and other network services that are the administrator’s responsibility or the solution architect.
If trust is the issue and data loss is the primary constraint, we (the service provider) or the client can physically back up the data. The physical backup may be local systems, servers, data centers, HDDs, other storage devices, etc.
Example 4: Suppose we have deployed our data on the cloud, and we are having threats regarding data loss or data spoofing. In that case, we can consider that we will back up data on a particular period basis like every weekend or every month-end or opt for manual methods that can be operated and managed physically. The physical storage can be anything like local machines, servers, on-premise architectures, etc.
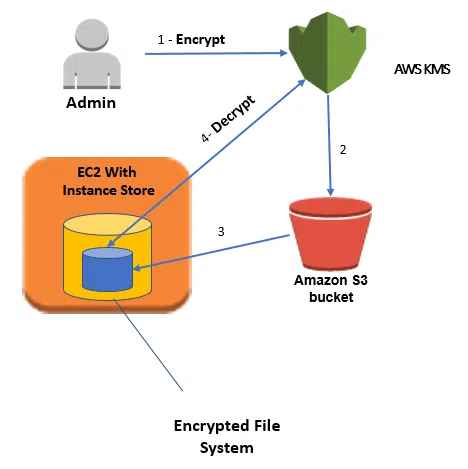
E) Cloud Provider Side Encryption
Cloud-side encryption uses client-side security services, which will be consolidated. Cloud-side predefined services will be applied on the client’s data to be processed and move further. Here at the server-side on the cloud platform, we will use a data encryption key (DEK) and a key encryption key (KEK). These services will encrypt and decrypt the migrated data.
F) Maximizing Security Policies on Gateway
Gateway is an essential component/module for cloud security. Because the gateway contains the firewall rules and policies, it states that more firewall rules will secure the cloud data more. It puts restrictions on inbound and outbound traffic to prevent unnecessary hits. Also, engineers can put HTTP, HTTPS, SSL, etc., filters on the cloud.
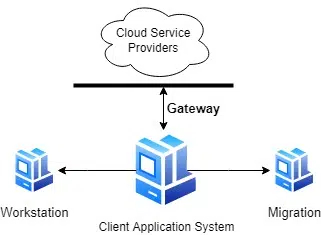
Example 4: Suppose we are implementing a payment gateway on our website. We have required SSL and HTTPS filters to allow network traffic from SSL and HTTPS packets. So, a gateway should be implemented to filter such incoming and outgoing packets, which only allows the HTTPS and SSL packets.
IV. Conclusion
From these brief researched topics, we can come up with many possible solutions in the cloud security platform. These parameters help users to choose a feasible platform wisely based on their enterprise requirements and need. Also, users can easily determine at which level the data on the cloud application is critical.
This blog is originally published at DZone.